Information Security Management System
ISMS
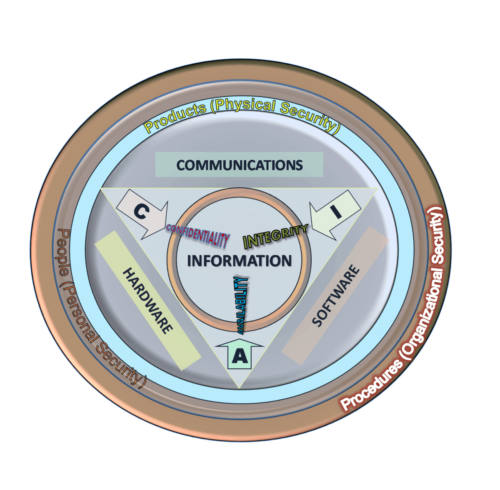
What is an Information Security Management System (ISMS)
An Information Security Management System is a collection of policies, procedures, and controls that systematically address information security in an organization. It is a framework based on risk assessment and risk management. The most widely recognized and instituted ISMS in the business environment is ISO 27001. It shares many of the features of a quality management system such as ISO 9001.
Because an ISMS is a management system it incorporates mitigation strategies beyond technical solutions such as firewalls and anti virus programs. As such, an ISMS must be designed to the specific requirements and risk profile of an organization. This would include the establishment of objectives for the establishment of security controls and the identification of all information assets within the organization (this includes electronic data, people, and paperwork.
Once these steps have been accomplished a risk assessment can be undertaken to identify and rank vulnerabilities. Involvement of all stakeholders is important in this process, including clients, customers, and supply chain participants. Then the necessary policies and procedures can be developed taking into account the specific regulatory requirements applicable for an organization’s industry.
These policies and procedures should not only involve mitigation strategies but should include incident response procedures in the event that a data breach should occur. As with many management systems, buy in from all levels of an organization is required starting at the top. Once instituted the program can be monitored, audited, and reviewed for effectiveness so that a continuous improvement cycle is in effect.
Why is an ISMS Important?
Organizations, both public and private face a growing threat of data breach. The Cyber Resilient Organization Report of 2020 found that 51% of organizations surveyed incurred a significant business disruption. Many of these attacks are being funded by nation/states intent on the theft of proprietary information and the disruption of business continuity. These threats to the confidentiality, availability, and integrity of data can result in the complete collapse of a business.
Threats from cyber incidents is not only targeted at conventional data bases but at infrastructure and manufacturing processes that use digital technologies. In fact every new technology introduced to an organization presents an entry point for a cyber crime to occur.
While the effective implementation of cyber security software solutions and security controls is essential, they can easily be compromised by lax physical plant security or a remote worker leaving a laptop unattended. That is why policies, procedures, and training are required for effective risk management.
 Information Security Management System Implementation and Certification
Information Security Management System Implementation and Certification
Implementing an ISMS is important to protect the confidentiality of information against threats and vulnerabilities. While a variety of systems that specify security controls, such as NIST SP 800-53 and CMMC, they do not incorporate effective risk management or process improvement. For those industries that must comply to these standards an ISMS can greatly facilitate the performance of these regulatory requirements.
ISO/IEC 27001 requires that an organization’s ISMS is compliant to the standard. Certification is therefore mandatory for recognition of a program. This is performed by an Accredited Registrar.
While the internationally the certification agencies may be referred to with differing titles, their function is the same. These include: certification bodies, registration bodies, assessment and registration bodies, “certification/ registration bodies, and sometimes registrars.
Certification against any of the recognized national variants of ISO/IEC 27001 (e.g. JIS Q 27001, the Japanese version) by an accredited certification body is functionally equivalent to certification against ISO/IEC 27001 itself.
Regardless of national variant of the standard, ISO/IEC 27001 certification, like other ISO management system certifications, usually involves a three-stage external audit process defined by the ISO/IEC 17021 and ISO/IEC 27006 standards:
ISMS Stage 1
Stage 1 of the process involves and informal review of required documentation. This would include checking for the completeness of the organization’s information security policy, Statement of Applicability (SoA) and Risk Treatment Plan (RTP). This stage serves as an orientation for both the auditor and the organization seeking accreditation.
ISMS Stage 2
The second stage towards accreditation involves a more detailed and formal compliance audit. This includes evaluation of the program against specific requirements of ISO/IEC 27001 standard.
At this point auditors seek evidence to confirm proper design and implementation of the program. This would include an evaluation of the performance of management and review functions (for example by confirming that a security committee or similar management body meets regularly to oversee the ISMS).
Certification audits are usually conducted by ISO/IEC 27001 Lead Auditors. Passing this stage results in the ISMS being certified compliant with ISO/IEC 27001.
ISMS Stage 3
Ongoing certification involves follow-up reviews or audits to confirm that the organization remains in compliance with the standard. This includes periodic re-assessment audits to confirm that the ISMS continues to operate as specified and intended. These should happen at least annually but (by agreement with management) are often conducted more frequently, particularly while the ISMS is still maturing.
CVG Strategy Information Security Management System Consultants
We can help you meet your information security management system goals. CVG Strategy QMS experts are Exemplar Global Certified Lead Auditors. We can provide the training required to understand and engage in a ISMS and make it meet desired objectives. This process includes defining the context of your organization, creation of internal auditing processes and much more. Contact us to learn more.
How Can We Help?
Take a look around our site and contact us for more information on how we can help you meet your challenges.
Latest News
Cyber-Intrusion and Data Exfiltration Concerns for BIS
Cyber-intrusion and data exfiltration are subjects of increased concern for the Bureau of Industry and Security (BIS). In its March 2024 release of Don’t Let This


