
DHS cybersecurity assessment criteria has been released that will set the bar for businesses seeking contract awards from the agency. The U.S. Department of Homeland Security has released this information to ensure that appropriate levels of “cyber readiness” are in place by its vendors. The DHS plan, released by Chief Information Security Officer Kenneth Bible, is being provided to its supply chain to facilitate feedback from industry business leaders prior to final roll out of the program.
Cybersecurity Readiness Factor Program
The Cybersecurity Readiness Factor program chosen by DHS differs from the the Cybersecurity Maturity Model Certification (CMMC) program approach embraced by the Department of Defense (DoD) in that it strives to create a more economically feasible solution for small businesses. Instead of requiring a certification process, the DHS is planning to use statistical analysis of questionnaire responses to determine contractor cybersecurity abilities to protect Controlled Unclassified Information (CUI). These questionnaire will query organizations on their ability to meet the security requirements of NIST SP 800-171r2 and NIST SP 800-172.
NIST SP 800-172 Enhanced Requirements
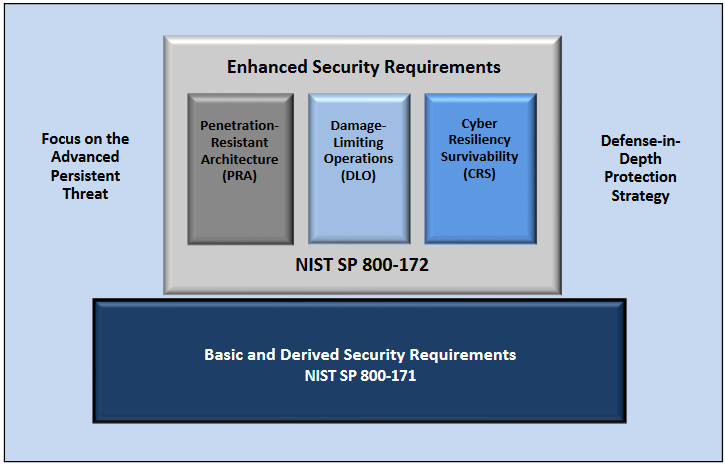
NIST SP 800-172 Enhanced Security Requirements for Protecting Controlled Unclassified Information is a supplement to SP 900-171 that contains recommended security enhancements for the protection of CUI that specifically address the entire Confidentiality, Integrity, Availability (CIA) triangle. While SP 800-171 focuses on confidentiality, SP 800-172 adds security controls to data integrity and availability to help achieve cyber resiliency and survivability.. This is achieved by detailing controls for penetration-resistant architectures and damage-limiting operations.
The standard describes the approaches used in the development of the enhanced security requirements. It then describes in detail the 14 families of security requirements. Supporting information is supplied in appendices including mapping tables and references. The figure below illustrates the relationships between NIST SP 800-171 and NIST SP 800-172.
DHS Criteria for Assessment
The proposed criteria for DHS assessments will rate businesses on perceived levels of readiness to protect CUI based on the numbers an types of security requirements in place. Levels of compliance are categorized as fully satisfied, partially satisfied, or not satisfied. Statistical analysis then provides three categories for likelihood for compliance:
- High Likelihood of Cybersecurity Readiness – The organization has implemented and understands the required technical controls for the protection of CUI.
- Likelihood of Cybersecurity Readiness – Organizations in this category are found to be between the fifteenth percentile and mean of DHS contractors engaged in the handling of CUI.
- Low Likelihood of Cybersecurity Readiness – This category comprises businesses in the lower fifteenth percentile of DHS contractors engaged in the handling of CUI.
Use of the Assessments at Present
The Cybersecurity Readiness Factor will be provided to the DHS Contracting Officer (CO) to aid the Source Selection Official in assessing contractor readiness. Because this methodology is comparative in nature, there is no strict pass/fail criteria and no offerors will be excluded from award eligibility. As such the evaluation will be used to conduct a best value tradeoff in decisions to award contracts. There may however, be requirements for submittal of a Plan of Action and Milestones (PoAM) after receiving contracts if the DHS has information security concerns.
Conclusions
Cybersecurity requirements for businesses involved with contracts with the federal government are going to continue to evolve. While clearly, the need to protect information is more important than ever, requirements can and are putting smaller business out of the game. This latest effort to reduce cost through the elimination of certification requirements is an interesting development but the costs associated with effectively implementing cybersecurity controls are still high.
CVG Strategy Information Security Management System Consultants
To assist businesses to meet the challenges in meeting DHS Cybersecurity Assessment criteria, CVG Strategy has developed an approach that combines the requirements of CMMC compliance with the ISO 27001 information security management system. This provides a coherent methodology for implementing and maintaining essential cyber security for businesses of any size.
We can help you meet your information security management system goals. CVG Strategy QMS experts are Exemplar Global Certified Lead Auditors. We can provide the training required to understand and engage in a ISMS and make it meet desired objectives. This process includes defining the context of your organization, creation of internal auditing processes and much more.
Identify Areas With CUI with CVG Strategy Signs
CVG Strategy also provides signs to identify areas containing CUI and export controlled items. These signs should be posted at all facility entrances where products are being produced or services are being performed that are under the control of the U.S. Department of State Directorate of Defense Trade Controls (DDTC) and are subject to the International Traffic in Arms Regulations per title 22, Code of Federal Regulations (CFR), Parts 120-130.


